When I received my new laptop at Hashicorp, I began personalising it as we all do. I used dotfiles to configure iTerm, and quickly pulled down Brew to get (almost) everything I needed installed.
Look into using their command line tool with the password manager: https://blog.agilebits.com/2017/09/06/announcing-the-1password-command-line-tool-public-beta/. Enable 1Password bookmarks; System Commands - File System - Check Eject and Eject All; File Navigation - Advanced - Check Escape path on 'Copy path to Clipboard' action; Terminal/Shell - Application - iTerm2; Terminal/Shell - Prefix - $ Extensions: Install Alfred Install Extension; Install and configure Nest Thermostat; Install VPN Toggle.
I would really love for 1Password for macOS to show suggestions for apps (like on Android and—occasionally—iOS). For example, my Quicken file is encrypted, and I store the password for that file in 1Password. This is what displays in 1Password when I click the menu bar icon with Quicken as the active application. Sudolikeaboss is a simple application that aims to make your life as a dev, ops, or just a random person who likes to ssh and sudo into boxes much, much easier by allowing you to access your 1password passwords on the terminal. All you need is iterm2, 1password. ITerm2 for better and more customizable terminal emulation - Choosy if you like to have multiple browsers for different purposes. Bitwarden instead of 1Password, because it's free and available everywhere. Swish instead of (or in addition to) Rectangle if you use a trackpad (which is the best and most ergonomic pointing device especially.

One of the first things I noticed that I didn’t have were the environment variables that normally read out of my bash profile. As I contemplated putting them in, I realised that it would be a lot more secure and a lot more portable if these were stored in 1Password (my personal secrets manager of choice).
Getting Familiar with the 1Password Schema
First up, I created a new 1Password entry, using the Password type. I called it “Environment Variables”.
I have put that entry into Edit mode in the image below so you can get a feel for the schema as it looks when you are setting this up in the UI.
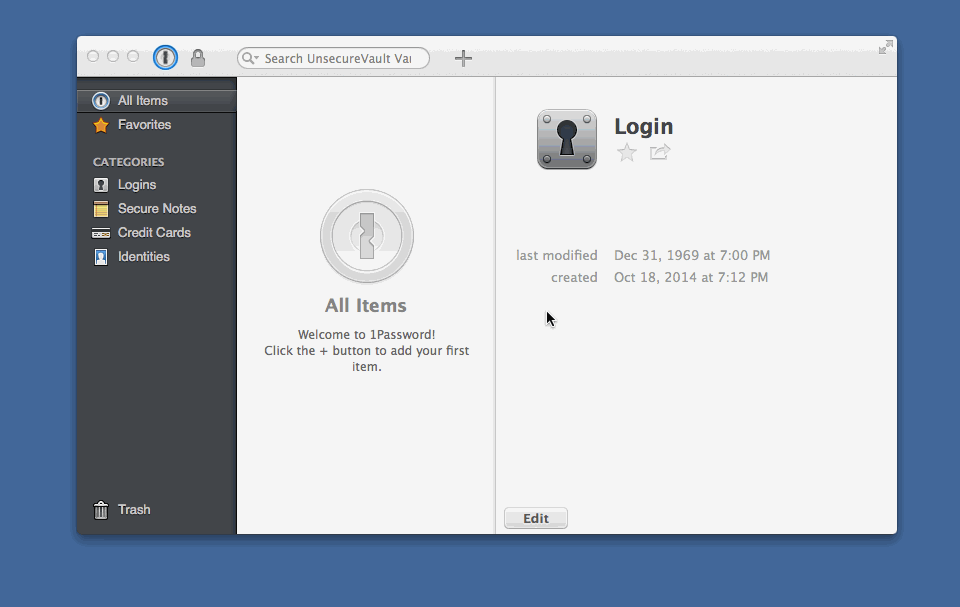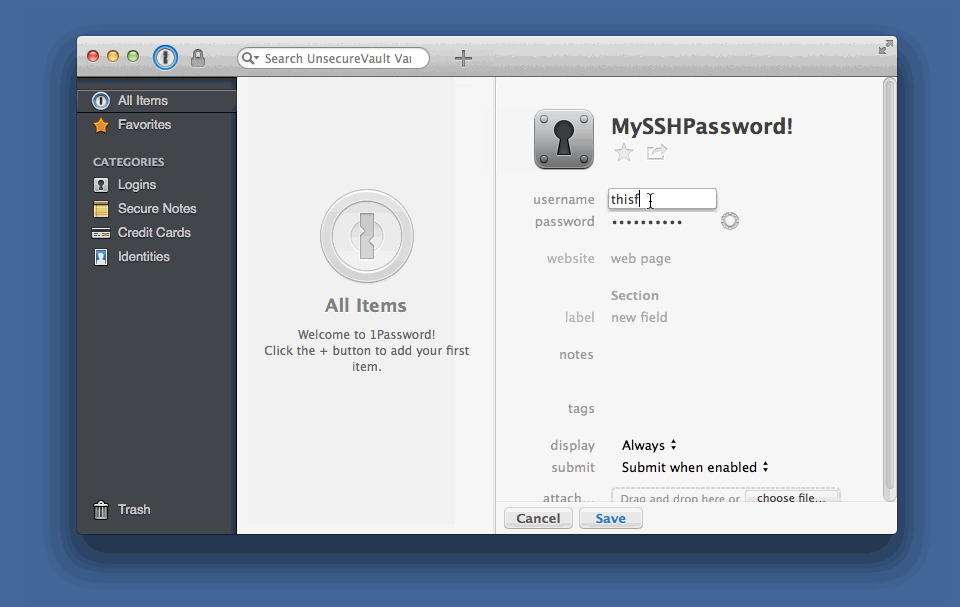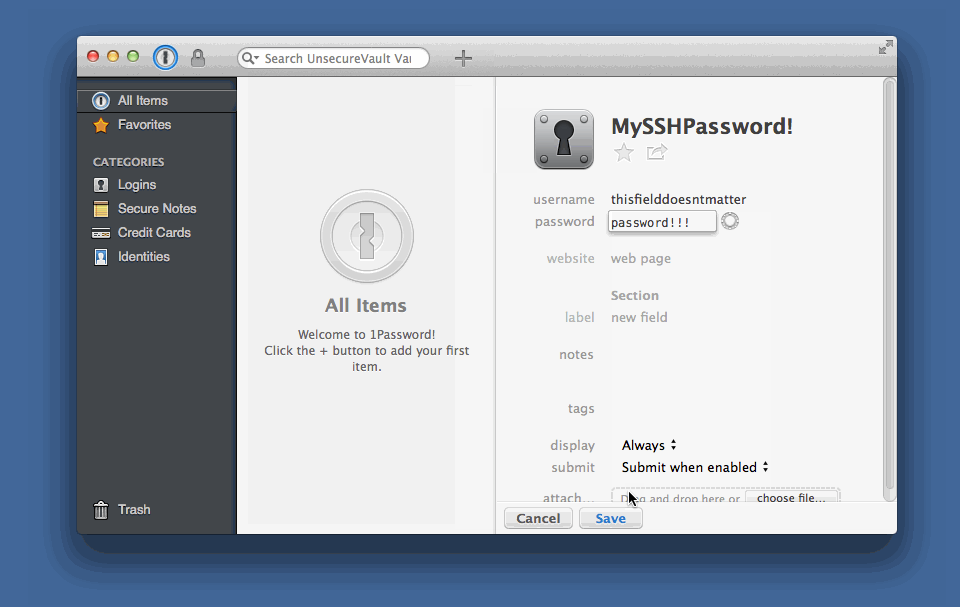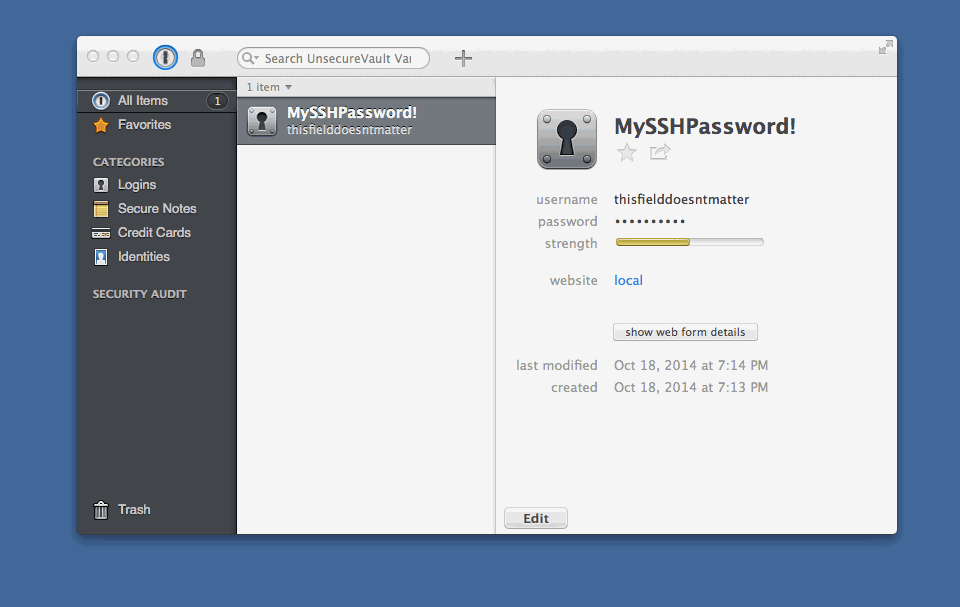
I named the Section as Environment Variables also, and created entries where the Label value matched the name of the environment variable I wanted to set. The value is… the value. You should also note from the screenshot that you can set the value type - I used “password” throughout in this case.

Next up, I grabbed the 1Password CLI and configured it per the official docs.
Once you’ve completed the configuration, login using eval $(op signin my)
Enter your master password, and if you’re using it your 2FA code.
Next up, you can run op get item 'Environment Variables' | jq . to get a better handle on the schema layout.
You’ll note that the first section ('.details.sections[0]) actually contains the name and title of your entry. As you can see in the image below, the second entry contains the details that we want to make use of.
Iterm2 1password Chrome Extension
The other thing that you’ll see here is that the key/value pair of the information that I’m after are represented by t and v respectively.
Iterm2 1password App
At this point, I thought I had enough of a handle on this to write it up as a bash script. The details of that are below.
Iterm2 1password Integration
To leverage this, simply source ~/.import_envvars.sh and away you go.
